Microsoft Sentinel –
discover what’s lurking below.
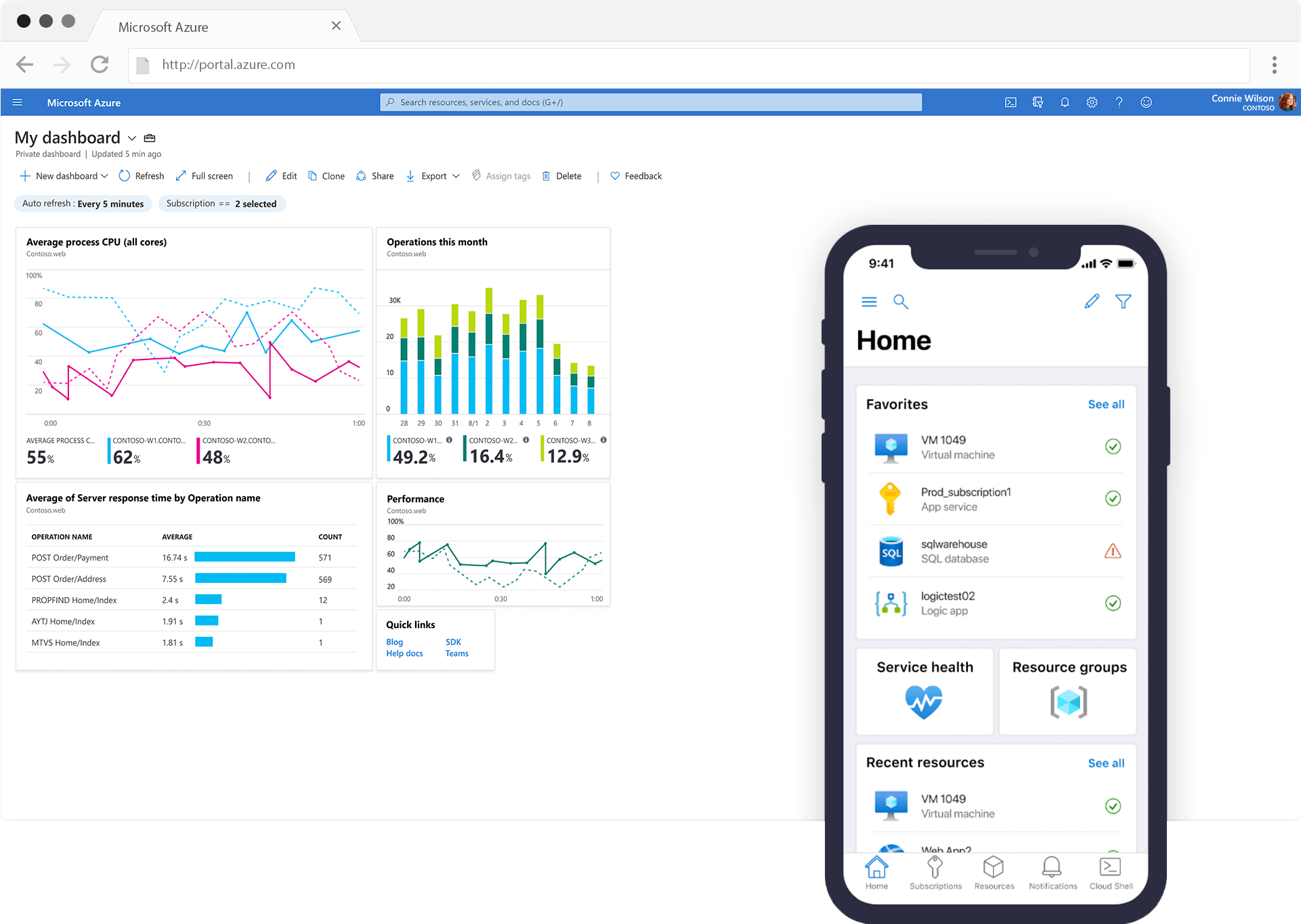
SIEM re-invented in the cloud to address today’s challenges of security analytics.
Microsoft Sentinel is one of the most capable SIEM tools on the market. Out of the box, Microsoft Sentinel is a powerful analytics tool that gives you visibility into security activity in your environment. The core AI & ML capabilities are second to none and will allow for much deeper security analysis. The AI & ML buzz words may make you feel overly confident in this out-of-the-box capability, but you need to really understand what you are doing to fully take advantage of the functionality. Sentinel leverages this technology to automate traffic analysis, but this may not always be relevant to your environment. Taking in the default analytics without considering the uniqueness of your environment may not allow you to catch a breach and will likely introduce a significant number of false positives. This is where the R2 Managed Sentinel offering comes in.
- Normalize data connector data to make it truly actionable
- Expertise that goes deeper than your average security firm
- Incident mitigation and recovery
- We make 'human' sense of Machine Learning to deliver you true awareness
- Custom delivered Playbooks to complete your SOAR lifecycle
- We work while you sleep with our 24/7 SOC
How it works

Baseline Setup

Log Sources & Consumption

Artificial Intelligence & Machine Learning

S.O.A.R.

Network Monitoring & Threat Detection

Visibility & Reporting
Microsoft Sentinel is the future of security analytics.
With Microsoft Sentinel you’re investing in security, security that will elastically scale to meet your needs – while reducing IT costs.
With simplified data collection across numerous sources, including Microsoft Sentinel, on-premises solutions and across clouds using built-in connectors. Connect with data from your Microsoft products in just a few clicks. Collect security data at cloud scale from any source.
By connecting relevant security logs into Sentinel, organizations can consolidate all their relevant data into one place. Utilizing Sentinel’s built-in Machine Learning and other detections, SOCs can now analyze their logs with ease and determine what truly malicious activity has taken or is currently taking place.
As a Microsoft Gold Partner, we are well-equipped to take your Sentinel implementation to the next level. Our extensive list of Microsoft competencies demonstrates our best-in-class capability and experience in delivering Microsoft technology and successful outcomes for our clients.

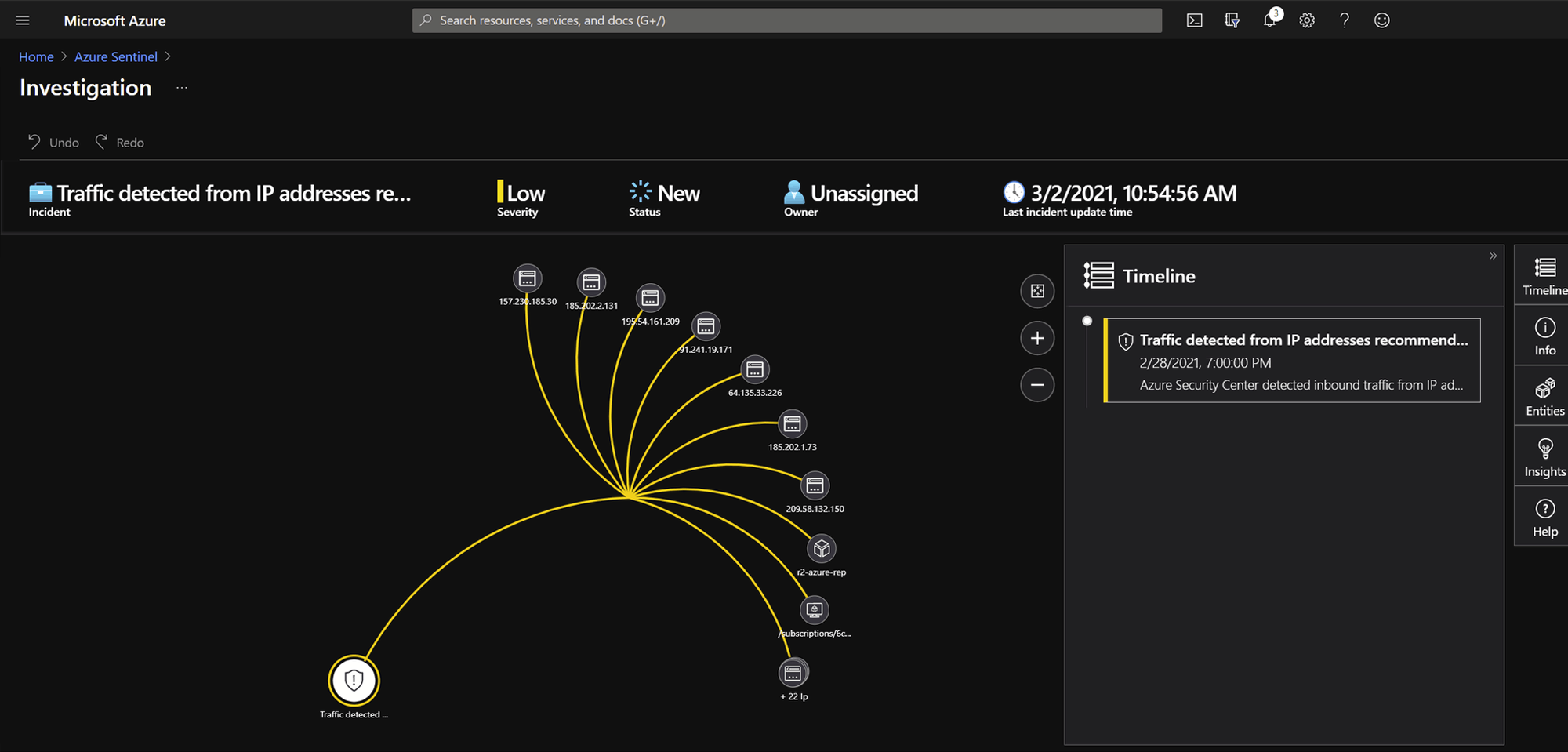
Investigations
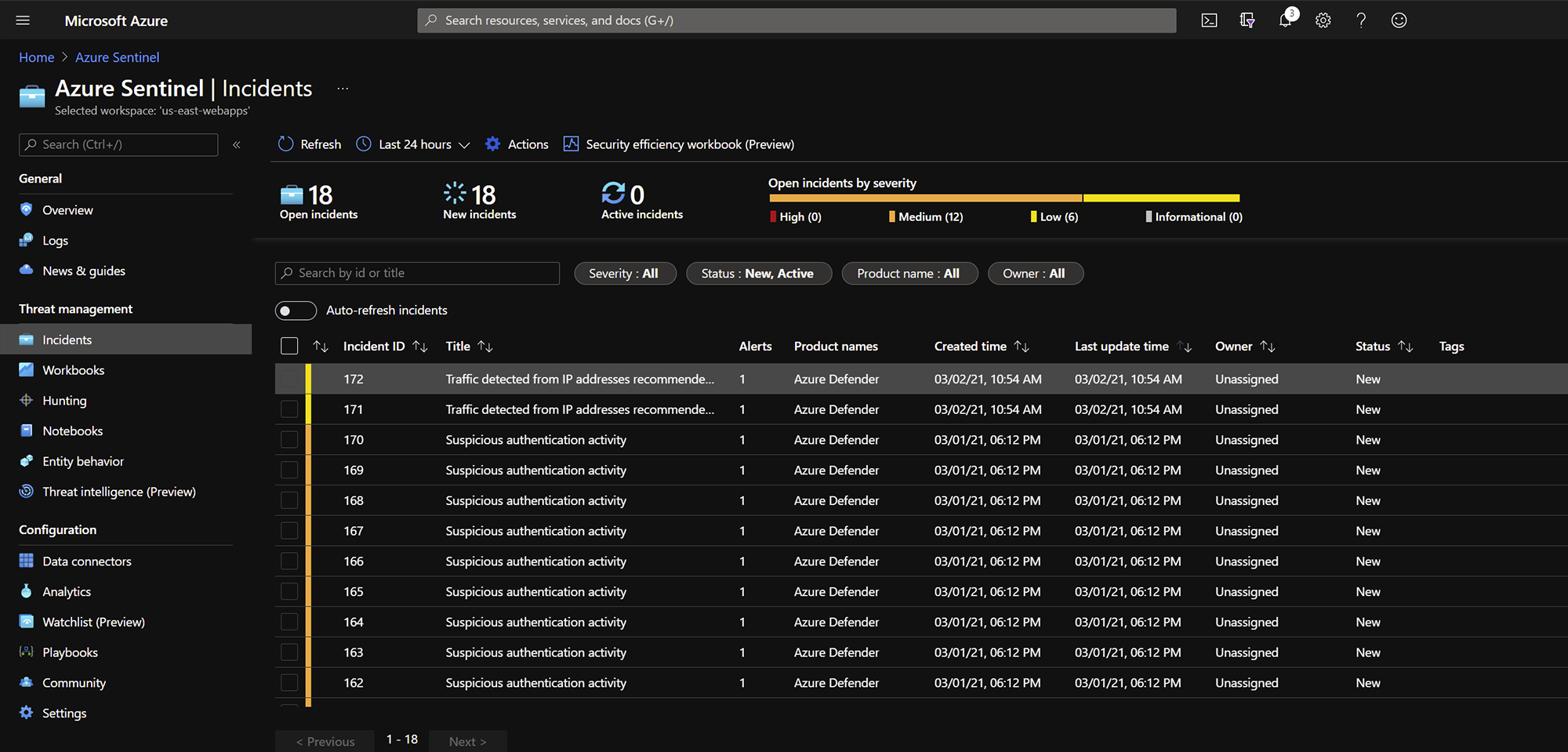
Incidents
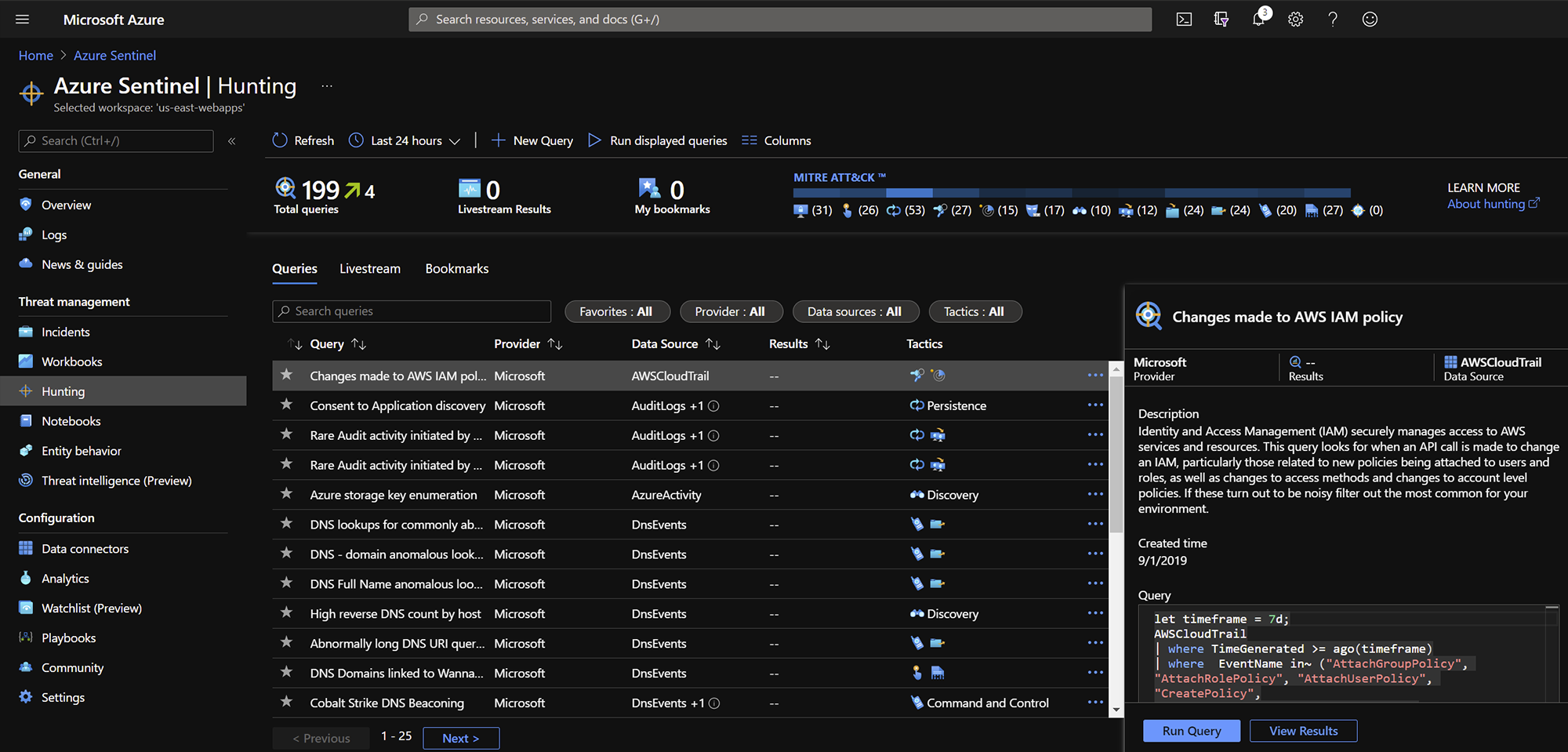
Threat Hunting
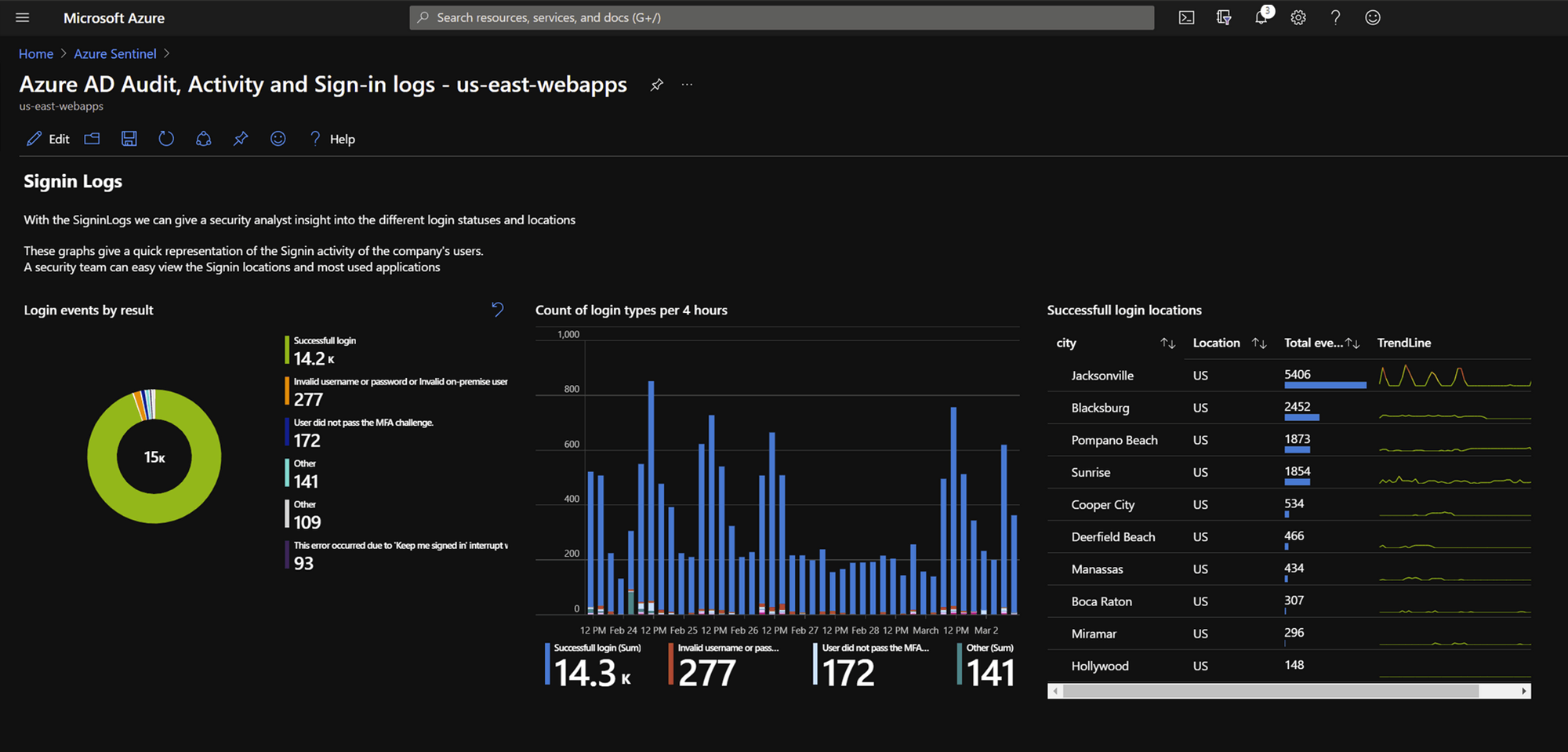
Azure Native Directory
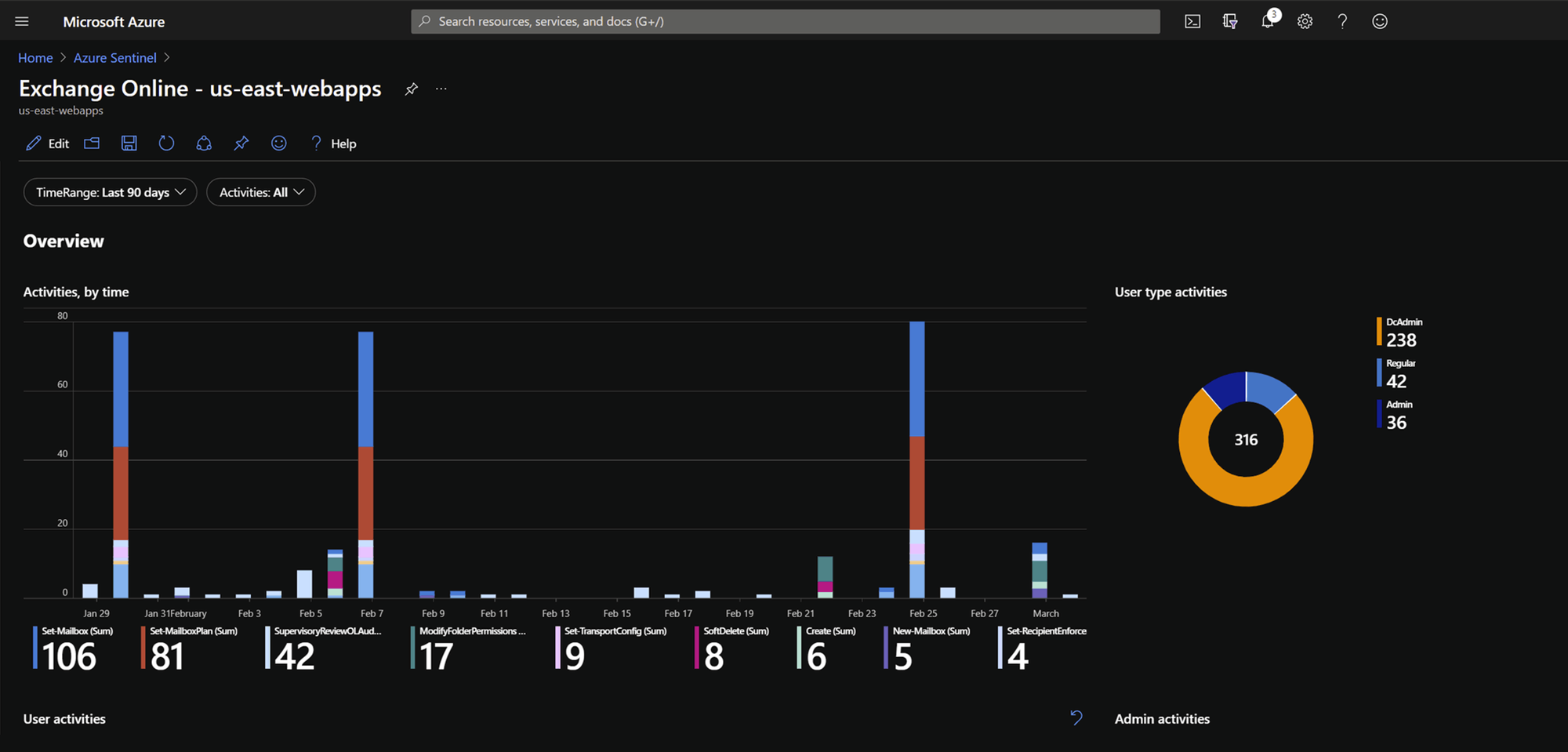
Azure Exchange statistics
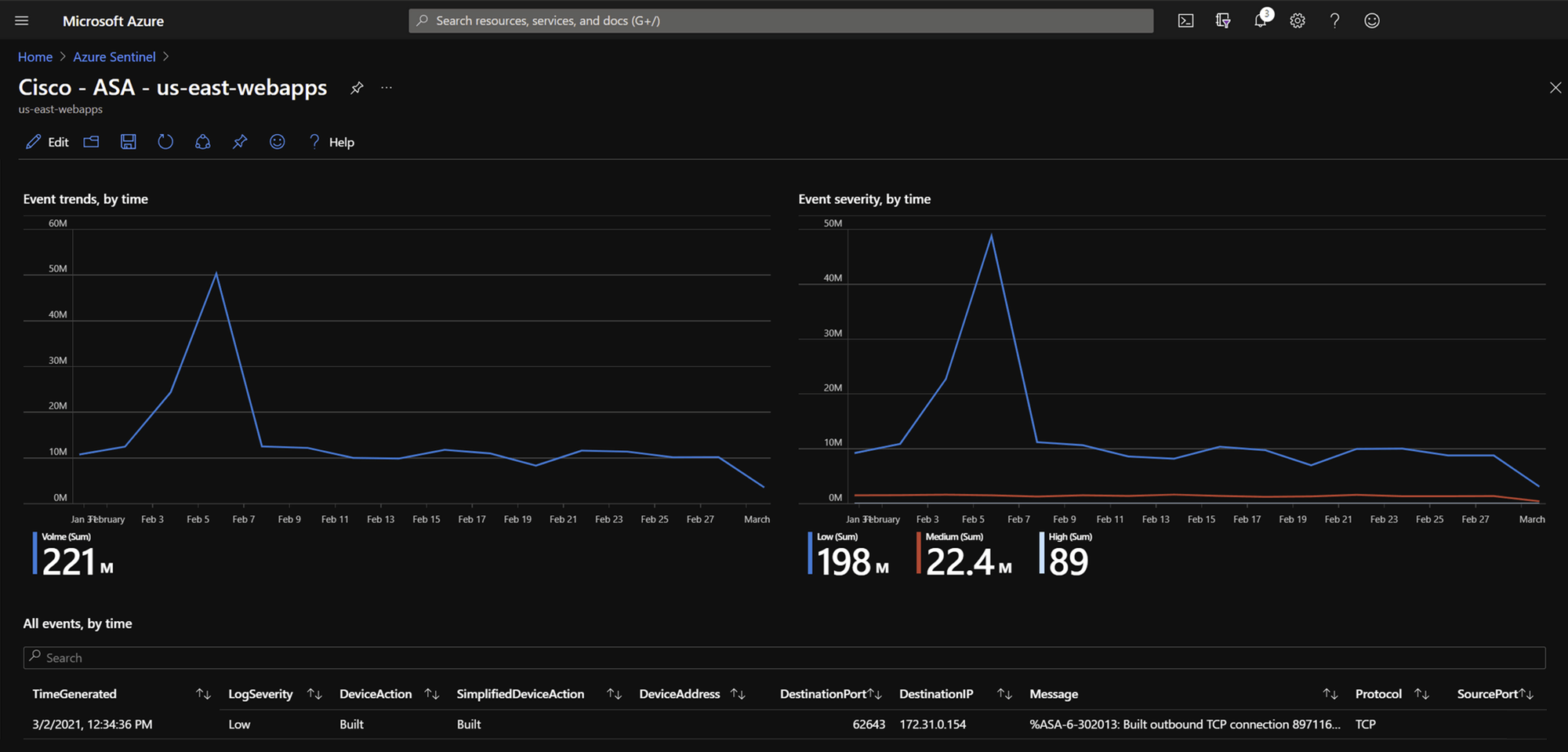
Cisco Connector
Shared responsibility
works with R2 on your side
The Shared Responsibility Model is a cloud security framework that delineates the obligations of cloud computing providers and its customers to disseminate accountability.
The first step to securing cloud workloads is understanding the shared responsibility model. The shared responsibility model for cloud security is one of those things that seems simple enough on the surface but is actually very complex when putting it into practice. Security will tend to be an afterthought for a large portion of users deploying workloads to the cloud. Adhering to a shared security responsibility model, means your security team maintains responsibilities for security as you move applications, data, containers, and workloads to the cloud, while the provider takes some responsibility, but not much.

Ask us anything.
We're here to help you step out of mediocre and into extraordinary.